Submitted by The Fan Club on

This guide is based on various community forum posts, and hours of frustration.
This guide is intended as a relatively easy step by step guide to:
- Disable Apache2 ModSecurity rules for Drupal and Wordpress.
- ModSecurity is a very powerful web application firewall but needs to be configured to work with Drupal and Wordpress.
- The ModSecurity rules can no longer be disabled in the .htaccess file and this guide explains how to disable the rules based on the specific location of a request on the server without having to disable rules for an entire domain in the httpd.conf file, by creating a local rule exceptions file.
Requirements:
- Webserver with ModSecurity setup and configured. Click here for How to install apache2 mod_security and mod_evasive on Ubuntu 12.04 LTS server
- Ubuntu/Debian based linux server is used as reference during tutorial but instructions are fairly generic for all implementations of ModSecurity.
1. View ModSecurity Audit Log File.
- We need to first find the rules that are being triggered by ModSecurity on your webserver.
- Open the tail end of the ModSecurity log file called modsec_audit.log to view the last entries made to the log file.
- For Apache2 servers it is located in /var/log/apache2/
- Open the Terminal Window and enter :
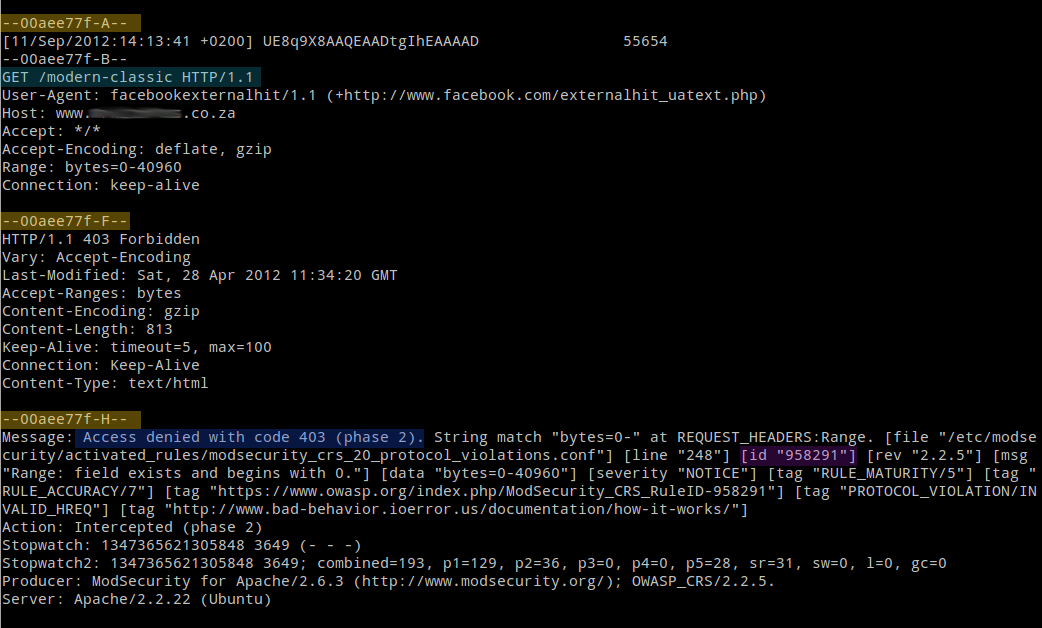
sudo tail /var/log/apache2/modsec_audit.log --lines 60 | less- The output should look similar to this screenshot below.
- Look for Access denied with code 403 and work backwards to find the start of the rule entry based on the log entry id.
- In this case the log entry ID is --00aee77f (see marked in yellow)
- Find the GET item - in this example it is /modern-classic (see marked in blue)
- Find the ModSecurity rule that was triggered by the GET - in this example the rule id 958291 (see marked in purple)
2. Create a Local Exceptions ModSecurity rule file.
- To disable / exclude certain ModSecurity rules you need to create a local exceptions file.
- There are various places you can create this file you only need to make sure that ModSecurity loads it during startup.
- We are going to create a whitelist.conf file in the /etc/modsecurity/activated_rules/ directory as all files with .conf extension will be loaded during ModSecurity startup.
- Open the Terminal Window and enter :
sudo vi /etc/modsecurity/activated_rules/whitelist.conf- For our example we add the location of the GET and ModSecurity rule id from step 1.
- Add the following to your whitelist.conf file and save :
<LocationMatch "/modern-classic">
SecRuleRemoveById 958291
</LocationMatch>
- You need to add the location as a regex of the directory path or file that is causing the ModSecurity rule to be triggered.
- In the following example we add the location directly to the file that triggers the ModSecurity rule.
<LocationMatch "/wp-admin/update.php">
SecRuleRemoveById 981173
</LocationMatch>
3. Restart Webserver.
- To the changes to take effect you need to restart you webserver.
- For Apache2 servers, open the Terminal Window and enter :
sudo service apache2 restart