Tor Tools is an application indicator and GUI frontend for the Tor proxy client service and other technologies to make your system totally private.
The Tor Browser does a great job as a private browser but there are many other applications communicating with the internet on your system.
Tor Tools was created to take advantage of the privacy offered by Tor for your Linux desktop.
How It Works
The Tor proxy service allows internet traffic to be directed via the Tor network. Any application that allows for the use of proxies can be setup to use the Tor proxy to connect to the internet. You can also set a system network proxy and applications that support this feature will automatically use the Tor proxy to connect to the internet. Important to note that although the service might be running on your system, traffic is not directed via the Tor network by default, system or application proxy support and setup is required. Tor Tools aims to streamline the use of Tor on Linux desktops.
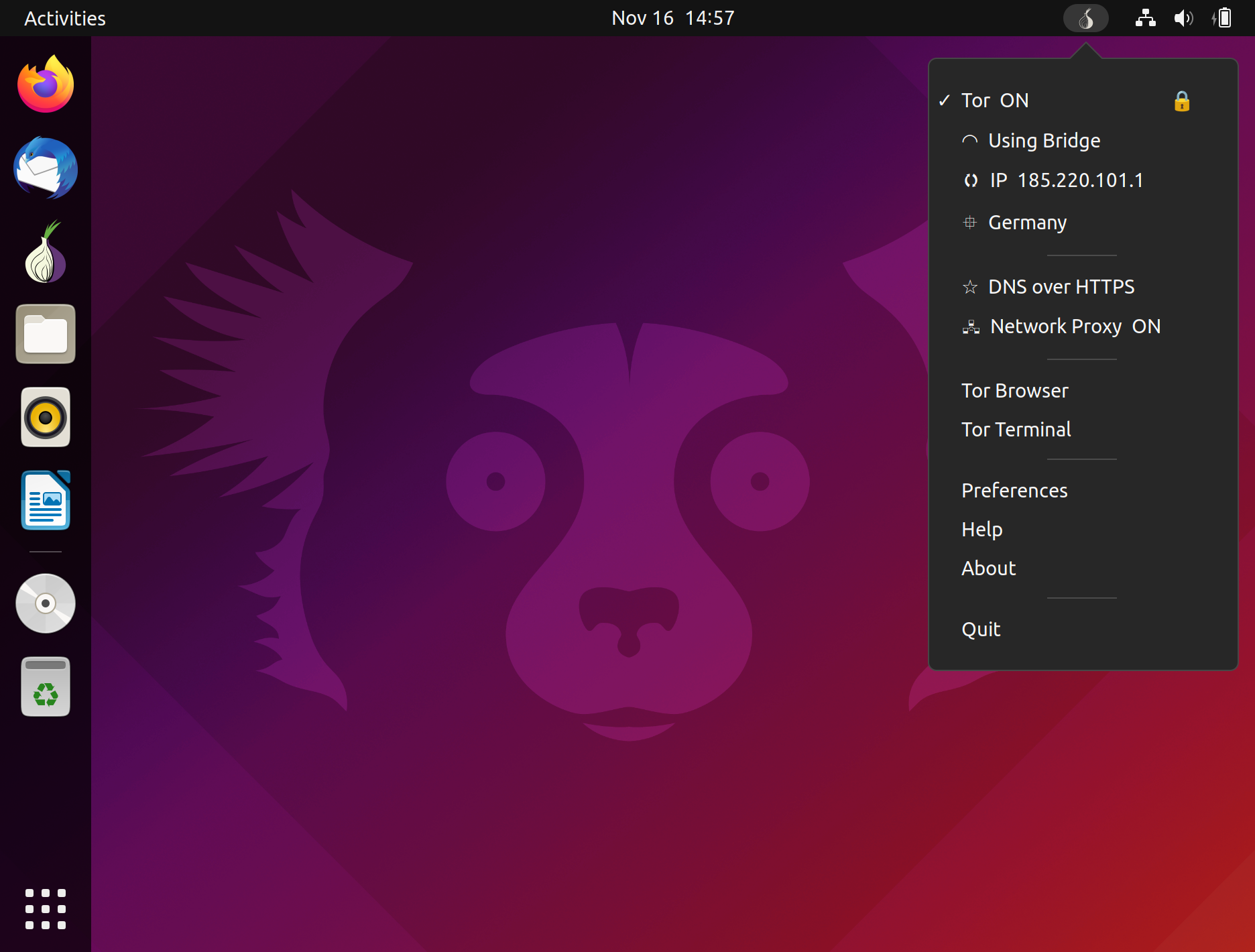
- Tor Tools will monitor the status, start / stop the Tor service and display your Tor IP and location (if available). You can click on the IP and request a new identity on the network. Clicking on the location will use OpenStreetMap to plot your IP location (if available).
- Tor Tools supports the use of Tor Bridges. Some governments, ISP’s and websites block all traffic from the Tor network as the exit nodes of the network are publicly available. Tor Tools uses obfs4 pluggable transports to enable Tor Bridges and conceal the fact that you are using Tor, but may slow down the connection compared to using ordinary Tor relays.
- Tor Tools controls the system network proxy. It interacts directly with the network settings to set the proxy on/off and also the socks host and port used. If your system does not support setting a system network proxy – Tor Tools will use the dconf settings that is present on most Linux systems to set and activate the system network proxy for Tor.
- The weak point in online privacy is the DNS server used by your system. Basically every internet name needs to be looked-up (resolved) on a DNS server that records the IP and what lookup was done. This is also usually done in plain text allowing for many bad things.
- To secure and keep your DNS lookups private, Tor Tools has implemented a DNS over Tor solution, or more specific the DNS Resolver for Tor developed by Cloudflare. When used in Tor Tools and all HTTP, TLS, HTTPS and UDP DNS requests are redirected to the Tor network. When DNS over Tor is deactivated the DNS will be reset to defaults. This feature does slow down your DNS lookups. (Currently only available in the Linux version)
Why use a DNS over Tor solution ?
“ First and foremost, resolving DNS queries through the Tor network guarantees a significantly higher level of anonymity than making the requests directly. Not only does doing so prevent the resolver from ever seeing your IP address, even your ISP won’t know that you’ve attempted to resolve a domain name.” - Cloudflare Blog
- Tor Tools supports DNS over HTTPS (DoH) as another option to secure your system DNS. Built in support for Cloudflare, OpenDNS, Google, Quad9 and Custom DNS over HTTPS providers.
Preferences
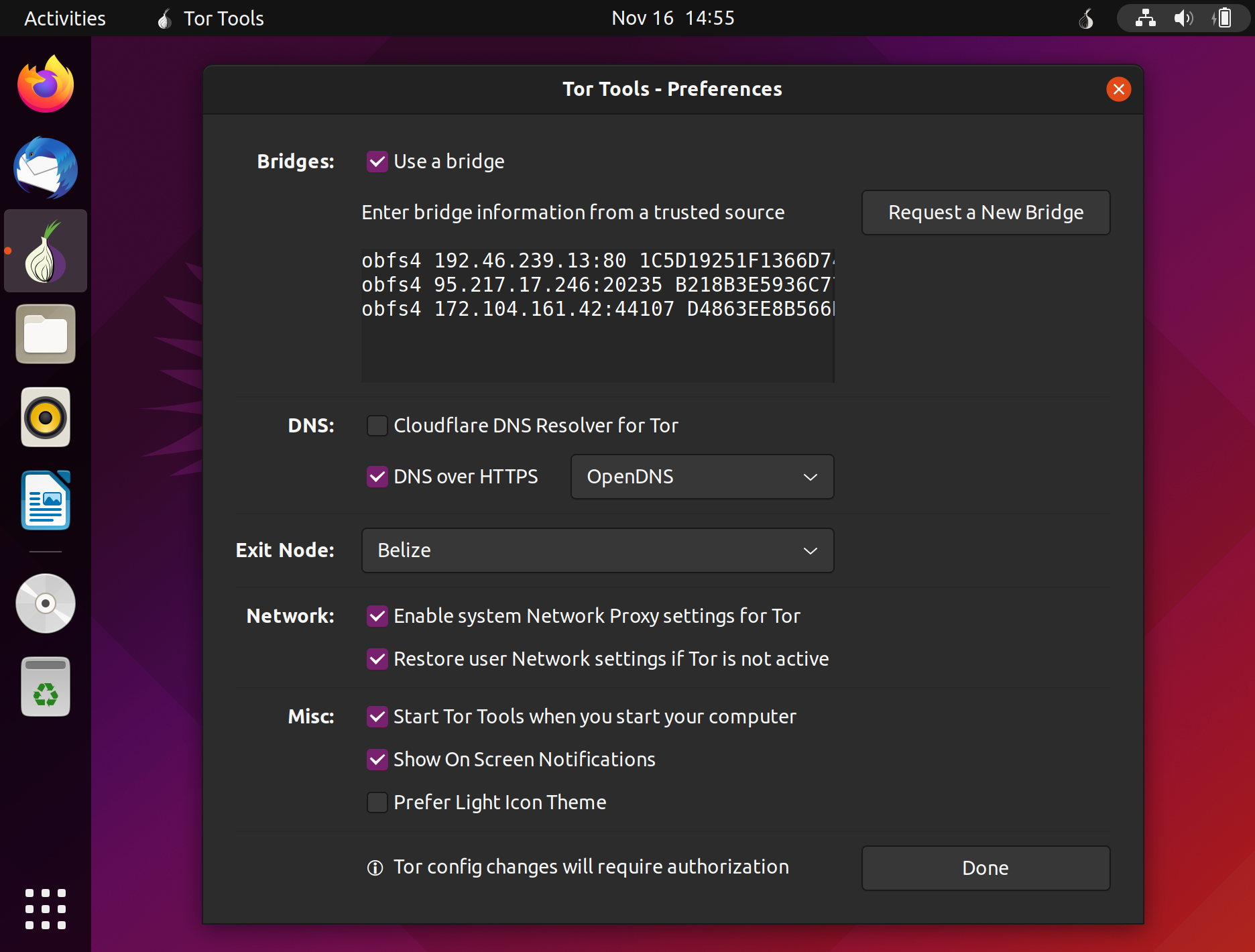
Bridges: When selecting the use of a Bridge you need to enter the bridge information. Click on "Request a New Bridge" and you will be directed to the Tor Bridges page where after entering Captcha code you will be given a list of bridges to copy and paste in the preferences.
DNS: Select the use of Cloudflare DNS Resolver for Tor or DNS over HTTPS .
Exit Node: By default Tor Tools will use the best available route and exit country. Here you can select a specific exit node country from a list of most available exit node countries. Note that even if a country is selected, there might not be an active node in that country available.
Network: Enable system Network Proxy settings for Tor will ebable the system network proxy. Tor Tools will automatically set the proxy host and port according to the Tor configuration. Restore user Network settings if Tor is not active will reset the user network settings to user default settings when the Tor proxy is set to OFF.
Misc: Various options to tweak the desktop experience. If you would like to see what Tor Tools is doing select "Show On Screen Notifications". If you cannot view the icon clearly in the task bar select the "Light Icon Theme".
Practical Use
- Select the Tor service, DNS over Tor and Network proxy in the Tor Tools menu for maximum privacy protection.
- Make sure you use application proxy settings and redirect to the Tor proxy socks host localhost and port 9050 or use the system network proxy settings if possible.
- For maximum privacy using Firefox, select Network proxy in the Tor Tools menu then in the Firefox got to Settings > Network Settings and select "Use system proxy settings", "Proxy DNS when using SOCKS v5" and "Enable DNS over HTTPS"
- If you have a problem using an application or connecting to a website use Tor Bridges or deselect "Network Proxy" in the Tor Tools menu and/or deselect using "Cloudflasre DNS resolver for Tor"
- When changing settings or waking from standby can cause Tor Tools to take a while to reconnect to the Tor network.
- To reset everything simply uninstall tortools.
Dependencies
- tor – Tor proxy client
- torsocks – Tool to redirect all application communication to the Tor socks port.
- obfs4proxy – Makes Tor bridges possible by using proxy obfuscating technology.
- socat – For redirecting DNS traffic
- cloudflared - For DNS over HTTPS support
Tor Tools will work with a current Tor install.
Debug
To enable the debug output and log file you can start Tor Tools from the command line with:
- Linux
python3 /opt/thefanclub/tortools/tortools -d The log file will be created in ~/.tortools.log
When starting Tor Tools without the debug flag, the log file will be deleted and all output disabled.